The information nation A Kremlin-managed research center is selling services that can deanonymize anyone in Russia
The Russian Presidential Affairs Department’s Scientific Research Computing Center develops systems to monitor and deanonymize social-media users, and it sells these systems to government and private clients alike. Using the services “PSKOV” and “Sherlock,” for example, insurance companies can root out dishonest employees, and security-guard companies can recruit new staff. “Poseidon,” meanwhile, allows the police to hunt down “extremists” online. Meduza has learned that these computing systems collect information on Russians not just from open sources, but also from leaked databases that are sold illegally on the black market. Many of those using these systems, moreover, are the same law-enforcement officials who leaked the private data in the first place. It turns out that it’s easier to conduct searches this way, outside the confines of formal police work.
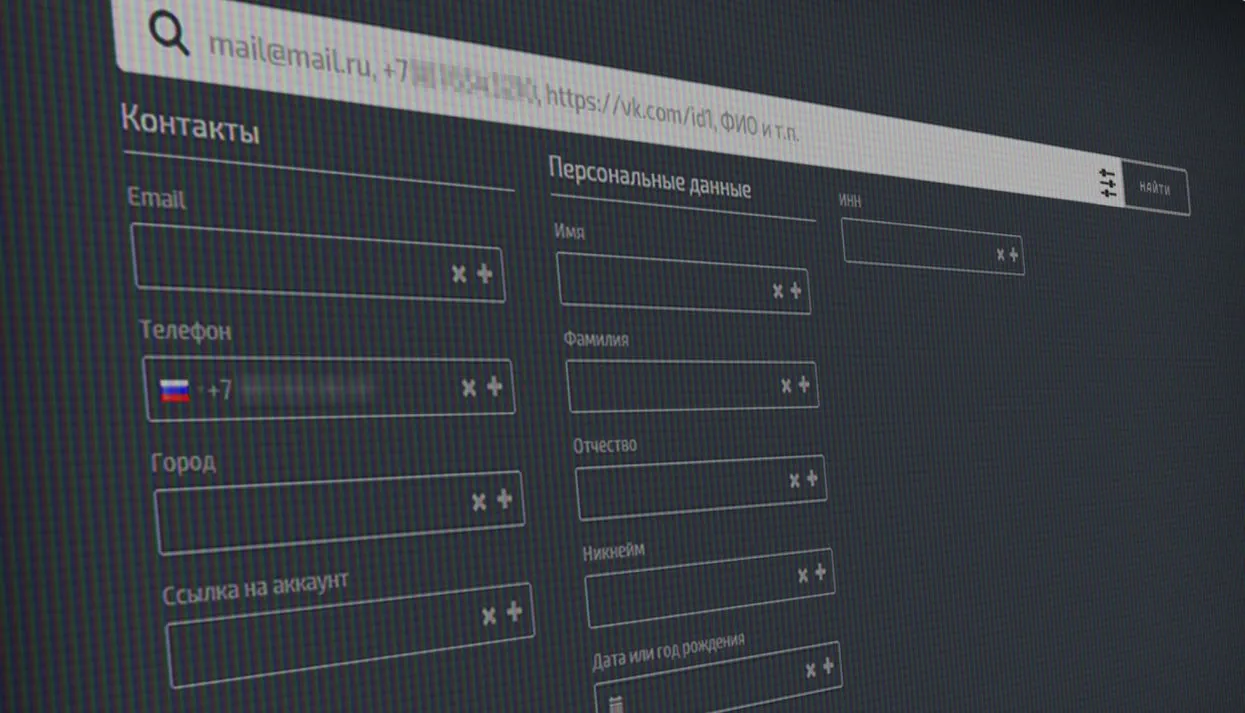
In the summer of 2017, one of Meduza’s sources at a major insurance company witnessed the presentation of two products from the Russian Presidential Affairs Department’s Scientific Research Computing Center (GRCC): “MediaMonitor” and “Sherlock,” which sales agents said would allow subscribers to retrieve the full résumé of any individual, including passport numbers, criminal records, and more — all with minimal initial data. Access to the systems cost 18 million rubles (almost $275,500) per month.
“MediaMonitor” allows clients to track the dissemination of specific news articles on social media. Enter a headline or URL, and you can view clusters of reposts online, displayed on a map of Russia, where you can zoom in to find the specific pages and IP addresses of users who shared the story you’re searching. GRCC insists that it can find individuals’ actual IP addresses — not just hosting providers’ IP addresses. To verify users’ identity and determine their physical address, GRCC’s clients also need access to another service called “Sherlock.”
“Sherlock”
Little is known publicly about “Sherlock.” Based on screenshots and presentation slides obtained by Meduza, the service can retrieve a wide variety of information about anyone in Russia, ranging from passport and vehicle identification numbers to foreign real-estate holdings. Experts told Meduza that this kind of information isn’t available from open sources, which means “Sherlock” pulls data from “gray” databases sold on the black market.
GRCC doesn’t advertise “Sherlock” (or any of its “special software”) on its website, but the company says its “FaceRadar” facial recognition software (which it compares to FindFace and FindClone) is “part of the ‘Sherlock’ services,” without explaining what that means. GRCC mentioned “Sherlock” again in a January 2018 press release about a group of students and lecturers from the Kikot Moscow University of Russia’s Interior Ministry learning to use the system.
There’s nonetheless strong evidence that “Sherlock” exists, and Meduza found nine sources who confirm that it is a functioning system. Three of these sources say they’ve actually used the service directly. Russia’s Interior Ministry declined to comment on these claims.
Meduza’s knowledge of “Sherlock” draws on (1) a police officer familiar with the system, (2) a security officer at one of Rostec’s subsidiaries who says he used to use the system, (3) Igor Bederov (a former detective and the founder of the “Internet-Rozysk”consulting and security audit service), who says he first heard about “Sherlock” in 2015, (4) Evgeny Venediktov, the director of the Center for Research in Legitimacy and Political Protest, which designed the social-media monitoring software “Laplace’s Demon,” (5) a staff member at one of GRCC’s competitors in the media-monitoring market, (6) a source in Russia’s biometrics market, who confirms that “Sherlock” actually works, unlike GRCC’s video-analysis service, and (7-9) three former GRCC employees.
Developer Valentin Dennikov (who likely works for GRCC) also published images of the “Sherlock” interface on his website. Based on this information, the system works like this:
- Enter an individual’s social-media page or email address.
- Get a dossier containing the individual’s full name, physical address, telephone number, birth date, tax number, state registration number, any companies or domain names registered in that person’s name, IP address, user ID, vehicle identification number, passport number, mobile phone provider, international mobile subscriber identity (the number that uniquely identifies every user of a cellular network), criminal record, and even foreign real-estate holdings.
According to sources who witnessed one of GRCC’s presentations, the company even demonstrated how “Sherlock” could find foreign property owned by Russian lawmakers previously investigated by anti-corruption activist Alexey Navalny. According to “Masterhost” co-founder Leonid Filatov, the operating logic here matches the intelligence community’s philosophy of “collect as much compromising information as possible about anyone and everyone — just in case.”
A spokesperson for the Russian Presidential Affairs Department, which supervises GRCC, told Meduza that the center doesn’t work with illegally obtained personal data. Some of the information retrieved by “Sherlock” and other GRCC services, however, is only accessible by violating privacy protections and possibly breaking laws on state secrecy. The center’s privacy-law offenses might have gone unnoticed by the public, if the GRCC hadn’t started courting private clients and expanding to commercial operations.
Customers in high places
GRCC’s main clients are Russia’s Defense Ministry and various police agencies. (As of November 2017, “Sherlock” was installed at 20 different Interior Ministry subdivisions.) The semi-secret research institute has contracts with classified defense enterprises, and the center’s own leadership is made up of veterans from Russia’s intelligence community. GRCC’s products also have significant commercial applications. For example, insurance companies use the software to identify dishonest agents, and microfinance organizations subscribe to the center’s services to maintain updated information about debtors.
In presentations for prospective clients, GRCC discusses the tasks of “modeling and forecasting the consequences of disruptions to the functioning of infrastructure,” citing Ukraine as an example. Former staff at GRCC told Meduza that both the Kremlin and Russia’s National Guard use the center’s products to vet candidates for major positions. A former programmer for the company told Meduza that officials use “Sherlock” to study candidates’ families on social media, digging up, for example, evidence of expensive gifts for their children that qualify as evidence of corruption and disqualify individuals for vacant posts.
GRCC’s services also help officials weed out politically unreliable volunteers at events that involve President Putin. For example, if candidates selected to join the audience at Putin’s annual televised “call-in” show have any social-media connections to anyone coded by GRCC as a “terrorist,” “anarchist,” or “libertarian,” they’re immediately barred from participation.
GRCC’s office building in Western Moscow
Liliya Yapparova for Meduza
GRCC, or the “Scientific Research Computing Center” federal state unitary enterprise, was created in 1985, and spearheaded by future Soviet Health Minister Evgeny Chazov, a medical-cybernetics enthusiast. One source in Russia’s biometrics industry told Meduza that GRCC is an “old defense research institute.” The company’s main office is located on Ryabinovaya Street in Western Moscow, just a 30-minute walk from “Kribrum,” a company managed by Igor Ashmanov, one of the few IT entrepreneurs in Russia who has defended the “Yarovaya” anti-terrorism laws, from which he has allegedly benefited personally, while working for other past state censorship efforts. Ashmanov told Meduza that he doubts a state enterprise like GRCC is capable of something as complex as “Sherlock,” which he describes as “a second Yandex.”
Multiple people who used to work at GRCC told Meduza that the center has deep ties to the police and military, often solving different issues without pay, while relying on the Defense Ministry for most of its revenue. “We said there aren’t any Russian soldiers in Syria or the Donbas, but they are there. And so we’re in a race against Bellingcat to geolocate all the posts where some idiot Russian soldier is taking selfies in a trench, posing with his rifle,” claims a former GRCC analyst, who says staff worked hard to delay the U.S. government’s discovery of the center’s existence.
Another former GRCC employee says Russia’s Defense Ministry once hired the company to calculate how an accident at a single Ukrainian power plant might affect the rest of the country’s power grid. The company later demonstrated the results of this study in a closed presentation, titled “Experience Solving Analytical Problems Based on Large Data Sets.” Asked about these materials, Defense Ministry officials refused to comment, and GRCC spokespeople referred Meduza to the Presidential Affairs Department.
A slide from GRCC’s presentation, “Experience Solving Analytical Problems Based on Large Data Sets”
One former GRCC staff member says Russia’s military also hired the company to model the number of troops and heavy equipment China would be capable of sending into Russia, in a theoretical armed conflict. GRCC allegedly discovered that all heavy equipment would enter Russia’s heartland via two railways, converging at the same bridge. Destroying this bridge, analysts concluded, could slow the advance of at least half of China’s weaponry. According to this story, China also realized this “risk,” and had ordered multiple “railway pontoons” from Rostec, which apparently broke its contracts after GRCC’s discovery. (Rostec told Meduza that these claims about a contract with China are inaccurate.)
Meduza also learned that GRCC apparently employs several hackers in its work with the police. In one case, a company specialist supposedly hacked a kidnapper’s social-media account to fool him into turning on his cell phone, in order to retrieve a recovery password via text message, which allowed the authorities to geolocate the device and find him. “Sometimes you can’t solve a problem without a hacker,” says a former employee with ties to the FSB.
Alexander Kolpakov
Alexey Nikolsky / TASS / Scanpix / LETA
Two former GRCC employees told Meduza that the center’s development activity exploded in 2014, when Alexander Kolpakov, a former Federal Protective Service (FSO) officer who reportedly supervised security as the presidential residences in Valdai and Novo-Ogaryovo, took over as head of the Presidential Affairs Department. Igor Bederov, a former detective and the founder of the “Internet-Rozysk”consulting and security audit service, says Kolpakov’s arrival transformed GRCC into one of the intelligence community’s main development platforms. But not everyone agrees with this assessment: Alexey Shcheglov, a former GRCC analyst, told Meduza that Kolpakov’s role wasn’t central, saying his appointment coincided with a “classic venture IT-company” moment for GRCC, when developers just out of college were free to realize their dreams. Another former employee says the center had essentially “limitless hardware capability,” with access to the Kremlin’s servers (rivaled in Russia only by Yandex). This equipment also added to the cost of GRCC services, which later drove the center to seek private clients.
By 2016, however, GRCC’s money started running out. The center’s only major commercial client was reportedly Rostec, and payment on several big government contracts were overdue. Without new business, the GRCC team started to disintegrate, with staff leaving for “Sbertekh,” “Rostelecom,” and “Mail.Ru,” says Alexey Shcheglov. This exacerbated the need for commercial sales, which led to sometimes desperate presentations like the one shared with Meduza.
“PSKOV”
In addition to “Sherlock,” GRCC has other products, like “PSKOV” (Poiskovaya Sistema Kategorii Osoboi Vazhnosti, or Special Importance Category Search Engine), which is capable of retrieving data from the anonymous Tor network, and “Poseidon,” which Russian police forces use to track extremism on social media. PSKOV’s interface once appeared briefly in a news report aired by the channel REN-TV about how federal officials used advanced technology to apprehend a spy.
In November 2017, one of the domain names of GRCC’s local area network (“Nevod,” or “Mesh,” at nevod.grcc.team) appeared in a news segment aired by REN-TV about the use of high-tech tools against spies. Meduza also located GRCC’s LAN domains apparently for “Sherlock” and “MediaMonitor.”
The interface for the PSKOV system
Known by developers as “the Russian Palantir,” the “PSKOV” system is registered with Russia’s Communications Ministry and is protected by a series of certificates of registration. Meduza obtained a 70-page description of PSKOV, which claims that it can produce whole dossiers about entire groups on social networks, search Tor traffic, analyze mass billing data, and find “hidden communications” between cell-phone subscribers using its “Calls” subsystem.
In early 2018, security officials reportedly approached GRCC and asked to use PSKOV to look into a “North Caucasian clan that was trying to elbow its way into power.” GRCC investigated roughly 40 people with the surname in question and discovered a hierarchical “close community” with ties to state officials and known criminals. Meduza’s source didn’t identify the family in question, but we obtained documents related to the investigation that included Instagram posts from Musa Tumgoev, who belongs to one of the most powerful teips (clans) in Ingushetia. It’s unclear how GRCC’s intelligence was used, but an FSB special operation in late 2018 led to Khasan Tumgoev’s arrest for embezzlement and theft. (Khasan Tumgoev’s family has major connections to the nuclear energy industry, and power industry generally.) Months later, in June 2019, Timur Tumagoev was convicted of fighting for the Islamic State in Syria, and there have been multiple uncited reports in the Russian media about “the Tumgoev brothers’ terrorist connections.”
“Gray” DBMS
The services designed by GRCC wouldn’t function without Russia’s highly developed black market for buying and selling leaked and stolen personal data through “gray” DBMS (database management systems). According to Meduza’s sources in law enforcement (where officials are responsible for leaking the personal data in the first place), the Interior Ministry and other police agencies fall back on GRCC’s services because it cuts through the red tape of formal investigative procedures. Aptitude with “gray” database management systems (like “Cronos” and “Sprut”) is a nearly required skill for anyone applying to work as security personnel at a major corporation in Russia, where many security staff are former intelligence agents.
In the United States, a system like Palantir operates legally because the database source material is often designed specifically for Palantir, with software engineers and the state working together. The Russian government doesn’t grant this kind of access to GRCC, however, at least not openly, so the company instead turns to leaked, illegally traded databases. Igor Bederov, the founder of “Internet-Rozysk” consulting and security audit service, says “Sherlock” connects to the “Sprut” database, one of Russia’s main “gray” database management systems.
In reality, Sprut is a search interface that in turn accesses other “gray” and “black” DBMS. “Sherlock” apparently has access to the Sprut API gateway, which accommodates direct requests and multiple back-end services.
Asked to list other “gray” DBMS in Russia, Meduza’s sources named “Cronos” (which dates back to the Soviet era), “Zvezda” (a collection of data from the North-West Bureau of Credit Histories, which had a contract with the Interior Ministry to receive information about individuals’ criminal records and loan applications), “Infolodzhik” (in St. Petersburg), “Prof” (in Yekaterinburg), and “Larix” and “Dofin” (two attempts by individual programmers with intelligence work experience to steal from existing databases and launch their own services using the information).
Russia’s first DBMS, like “Cronos,” appeared before the fall of Communism. Initially, these databases were sold physically on discs and hard-drives in markets (at Mitinskoe in Moscow and “Yunona” in St. Petersburg), but today access to this private information is traded in specialized online forums.
Cronos was initially a KGB initiative to store citizens’ personal data. During Perestroika, agents left the service and decided to commercialize the database, selling copies illegally. Top officials in law enforcement neither encouraged nor hindered this black market, as the chaos that beset Russia’s post-Soviet police force meant officers needed all the help they could get when it came to investigative work. Meduza’s sources say Russia still relies on “gray” databases like Cronos for express credit checks, which supposedly wouldn’t be possible using the available legal services. Roskomnadzor, Russia’s federal information regulator, declined to answer Meduza’s questions about why the state doesn’t crack down on illegal DBMS.
The competition
Besides “Sherlock” and other GRCC products, there are many competing services on Russia’s media-monitoring market that can deanonymize Internet users. Rivals also rely on a variety of information sources, including leaked databases of different online services (like the online retailer WildBerries.ru). For example, the “Internet-Rozysk” (Internet Search) consulting and security audit service helped police in Yekaterinburg identify activists using Telegram chats during protests between May and June 2019 against the construction of a new cathedral. The company also helps find chat rooms used by pedophiles and helps deanonymize participants.
In May 2019, Igor Bederov’s “Internet-Rozysk” consulting and security audit service helped police in Yekaterinburg by fielding bots in a Telegram group chat used by local protesters. The bots proposed separate rallies and roped individuals into sharing personal details that were then fed into Bederov’s “TelPoisk” service, which learns what it can about people from open sources (such as social networks and employment websites).
Bederov’s also been working with Evgeny Venediktov, the director of the Center for Research in Legitimacy and Political Protest, which designed the social-media monitoring software “Laplace’s Demon,” to collect information in “pedophile group chats” and deanonymize the participants, in order to determine if any of the individuals work with children. Venediktov has another program called “Insider Telegram” that he says can deanonymize users with just a telephone number. (He has access to leaked Wildberries.ru retail records, which allows him to connect phone numbers to the names and addresses listed on orders.) Venediktov acknowledges that these searches might violate privacy laws, but he claims this access is only for demonstration purposes and isn’t actually sold to clients. Using this approach, police can effectively skip dozens of bureaucratic steps in a criminal investigation. (Meduza‘s sources claim, however, that officers often use illegal intelligence tools not for police work, but in personal searches, hunting down information about themselves, relatives, or even junk callers.)
Russia also has a legal “business intelligence” industry that relies entirely on open source data, though even here there are legal complications. “Double Data” and Artur Khachuyan’s “Tazeros Global Systems,” for example, have both run into conflicts with major social networks for collecting large amounts of users’ data. Facebook previously demanded that Khachuyan’s company stop snooping on its users, and VKontakte wanted to ban “Double Data” from selling its users’ open data.
The main business model of “Double Data” and similar companies is finding potential clients for banks and insurers. For example, these companies use information from court officers and credit bureaus to identify people who need to refinance, and then sell their data to microfinance institutions; they update records for collectors; and they identify fraudsters. An insurance company might see that it’s paying out unusually large claims in a certain area, and hire a firm like Double Data to study the open-source data available about the company’s clients, and learn about suspicious connections to local insurance agents.
“Sherlock 2.0,” the Interior Ministry, and SORM
In recent years, GRCC has tried to court private clients, sometimes making claims in sales presentations that seem to indicate illegal access to state intelligence.
By the fall of 2018, when a GRCC presentation to the Interior Ministry’s Central Office mentioned “Sherlock 2.0,” Igor Bederov says the service now monitors not only social networks, but also has access to “the closed API of Mail.Ru Group products,” potentially including VKontakte and Odnoklassniki. Mail.Ru Group told Meduza that such third-party access is “unthinkable,” but social networks don’t reveal who has access to their closed API, and Russian anti-terrorism laws could force “information-distribution organizers” to register with the state and share sensitive data, says Karen Kazaryan, the managing director of the Internet Research Institute.
Multiple sources told Meduza that GRCC presentations to the Interior Ministry included clear signs that an updated version of “Sherlock” has access to social networks’ API shared with Russian intelligence agencies. In GRCC sales demonstrations, for example, searches revealed the IP addresses, telephone numbers, and email addresses privately assigned to various accounts (not the information publicly displayed to friends). A former “Sherlock” developer who left GRCC in 2017 told Meduza, however, that the center only has open API access, and Facebook’s open API alone was so much that GRCC limited itself to processing photographs, profile pictures, and names.
GRCC’s stand at the Interpolitex 2017 exhibition
GRCC
Sources who witnessed GRCC’s Interior Ministry presentation say they were told that the new “Sherlock” pulls data not from “gray” DBMS, but directly from the Interior Ministry’s own databases and cellular providers’ databases. But a former “Sherlock” developer denies this, saying that source data was always leaked from individual law enforcement officers with specific search requests.
GRCC’s attempts to monetize access to Interior Ministry data, moreover, apparently hurt sales to police departments. A source in the ministry told Meduza that officials largely rejected “Sherlock 2.0” as GRCC’s attempt to sell back the ministry’s own leaked information. The ministry’s Central Office apparently signed just two contracts for annual workstations, spending a total of 900,000 rubles (about $14,110). According to Igor Bederov, GRCC essentially ended up giving the service away to friendly clients, losing hundreds of millions of rubles and the revenue needed for further development.
In “Sherlock” presentations, GRCC also suggests that it has access to data from SORM (Sistema Operativno-Razysknykh Meropriyatii, or System for Operative Investigative Activities), the system developed by the Federal Security Service for wiretapping telephone conversations and monitoring Internet traffic. The system’s latest iteration — SORM-3, which is supposedly capable of collecting and storing data from all types of communications (from telephone calls to Internet traffic, all in real time) for long periods of time — was supposed to come online a couple of years ago, in accordance with the so-called “Yarovaya anti-terrorist laws.” Sources told Meduza, however, that SORM-3 still doesn’t work yet, and the access GRCC mentions to customers is just a sales pitch. If companies did have access to SORM data, it would constitute a breach of state secrets. As it is, accessing leaked databases traded illegally is already a violation of Russia’s privacy laws.
Story by Liliya Yapparova, edited by Alexey Kovalev
Summary by Kevin Rothrock
Meduza’s knowledge of “Sherlock” draws on (1) a police officer familiar with the system, (2) a security officer at one of Rostec’s subsidiaries who says he used to use the system, (3) Igor Bederov (a former detective and the founder of “Internet-Rozysk”consulting and security audit service), who says he first heard about “Sherlock” in 2015, (4) Evgeny Venediktov, the director of Center for Research in Legitimacy and Political Protest, which designed the social-media monitoring software “Laplace's Demon,” (5) a staff member at one of GRCC’s competitors in the media-monitoring market, (6) a sour
GRCC’s FSO ties
The Federal Protective Service plays a significant role in the electronic communications between state agencies in Russia. In July 2019, journalists learned that the FSO will receive 1.4 billion rubles ($21.8 million) to develop RSNet (the Russian State Network), which builds on the Russian Government Internet Network. The Presidential Affairs Department won’t respond to rumors that GRCC is participating in this project, however, and spokespeople told Meduza that it’s wrong to tie Kolpakov’s former position to GRCC’s current work. The FSO declined to speak to Meduza.